mirror of
https://github.com/stefanpejcic/openpanel
synced 2025-06-26 18:28:26 +00:00
174 lines
8.3 KiB
Markdown
174 lines
8.3 KiB
Markdown
---
|
|
hide_table_of_contents: true
|
|
---
|
|
|
|
|
|
# 0.1.9
|
|
|
|
Not yet released.
|
|
|
|
|
|
### 🚀 New features
|
|
- OpenAdmin Notifications Center is now using [Sentinel](https://github.com/stefanpejcic/Sentinel/tree/main) service
|
|
- [IPset Blacklists for UFW](#ipset-blacklists)
|
|
- [Restrict access to Cloudflare only with a single click](#cloudflare-only)
|
|
- [OpenPanel FTP - FTP module for OpenPanel (**BETA**)](#ftp)
|
|
- [OpenMail - Emails module for OpenPanel (**BETA**)](https://github.com/stefanpejcic/OpenMail/)
|
|
- [`opencli faq` command to show frequently asked questions](#opencli-faq)
|
|
|
|
### 🐛 Bug fixes
|
|
- Fixed bugs with `opencli admin disable` and `opencli admin enable` commands.
|
|
- Fixed bug with `opencli report` that failed to retrive MySQL version for mysql running inside docker container.
|
|
- Fixed bug with incorect version in changelog link on *OpenAdmin > General Settings > Update Preferences*.
|
|
- Fixed bug with update script
|
|
-
|
|
|
|
|
|
### 💅 Polish
|
|
- [Custom SSH Welcome message](#ssh-welcome)
|
|
- Working server time on OpenAdmin > Dashboard.
|
|
- CPU type information on OpenAdmin > Dashboard.
|
|
- [Cloudflare IP addresses are now highlighted in OpenAdmin > Firewall](https://i.postimg.cc/xTDPTG6S/image.png)
|
|
- Install script now supports optional flags `--enable_ftp` and `--enable_mail` to enable experimental features.
|
|
- `opencli -v` is now an alias for `opencli --version`.
|
|
|
|
|
|
## FTP
|
|
|
|
New experimental OpenPanel FTP module is now available and allows you to create FTP sub-accounts.
|
|
|
|
Upon activation, a fresh Docker container featuring VSFTPD will be initiated, serving as a shared environment for all OpenPanel FTP sub-users. This ensures the segregation of FTP accounts from other processes and services. Even in the event of a compromise, the impact is contained within the confines of the OpenPanel user's home folder, preventing access to other services or files.
|
|
|
|
This functionality leverages the [open-source OpenPanel FTP module](https://github.com/stefanpejcic/OpenPanel-FTP/) and is currently in its preliminary developmental phase. As such, it is not enabled by default and there are no additional options available in the OpenPanel interface to facilitate the creation and management of FTP users. Currently, all configurations must be performed by the administrator via the terminal:
|
|
|
|
To install FTP on an OpenPanel server, execute the following command:
|
|
```bash
|
|
opencli ftp-setup
|
|
```
|
|
|
|
To create new FTP accounts:
|
|
```bash
|
|
opencli ftp-add <NEW_USERNAME> <NEW_PASSWORD> <FOLDER> <OPENPANEL_USERNAME>
|
|
```
|
|
|
|
After detailed testing, a dedicated FTP page will be introduced to the OpenPanel, enabling users to seamlessly create FTP sub-users.
|
|
|
|
## Cloudflare only
|
|
|
|
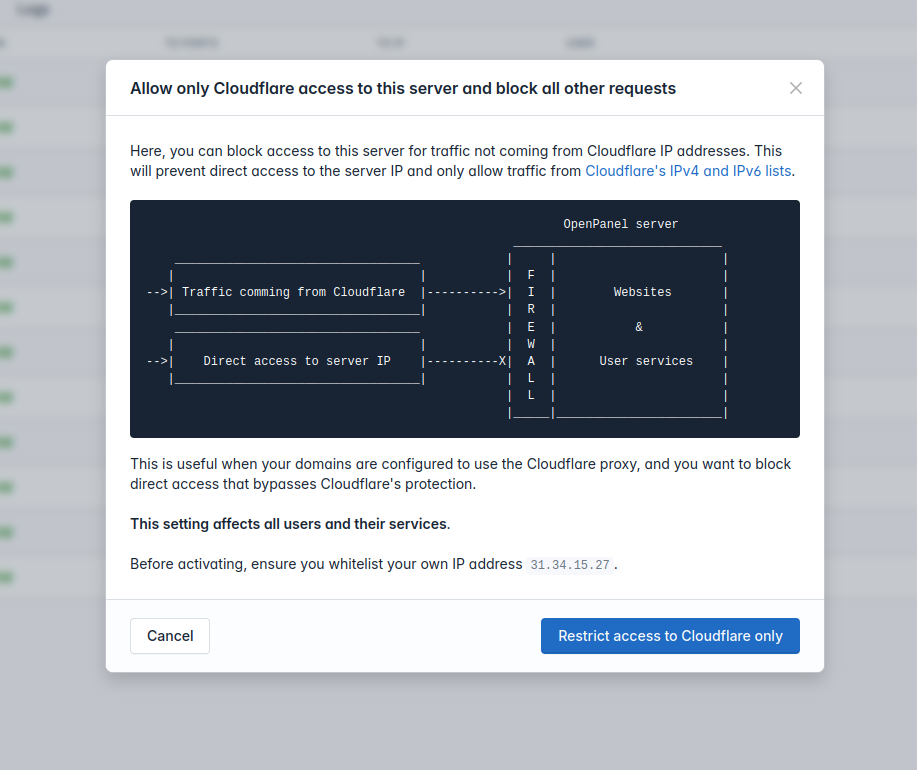
Administrators can now disable direct server access and only allow access via Cloudflare proxy.
|
|
|
|
```bash
|
|
OpenPanel server
|
|
_____________________________
|
|
__________________________________ | | |
|
|
| | | F | |
|
|
-->| Traffic comming from Cloudflare |---------->| I | Websites |
|
|
|__________________________________| | R | |
|
|
__________________________________ | E | & |
|
|
| | | W | |
|
|
-->| Direct access to server IP |----------X| A | User services |
|
|
|__________________________________| | L | |
|
|
| L | |
|
|
|_____|_______________________|
|
|
```
|
|
|
|
To enable this feature simply navigate to OpenAdmin > Firewall and click on the Cloudfare button.
|
|
|
|
|
|
|
|
Or from terminal:
|
|
|
|
- Enable Cloudflare restrictions:
|
|
```bash
|
|
opencli cloudflare --enable
|
|
```
|
|
- Disable Cloudflare restrictions:
|
|
```bash
|
|
opencli cloudflare --disable
|
|
```
|
|
|
|
This feature will regularly update Cloudflare ip addresses to make sure new CF IP ranges are included.
|
|
|
|
## IPset Blacklists
|
|
|
|
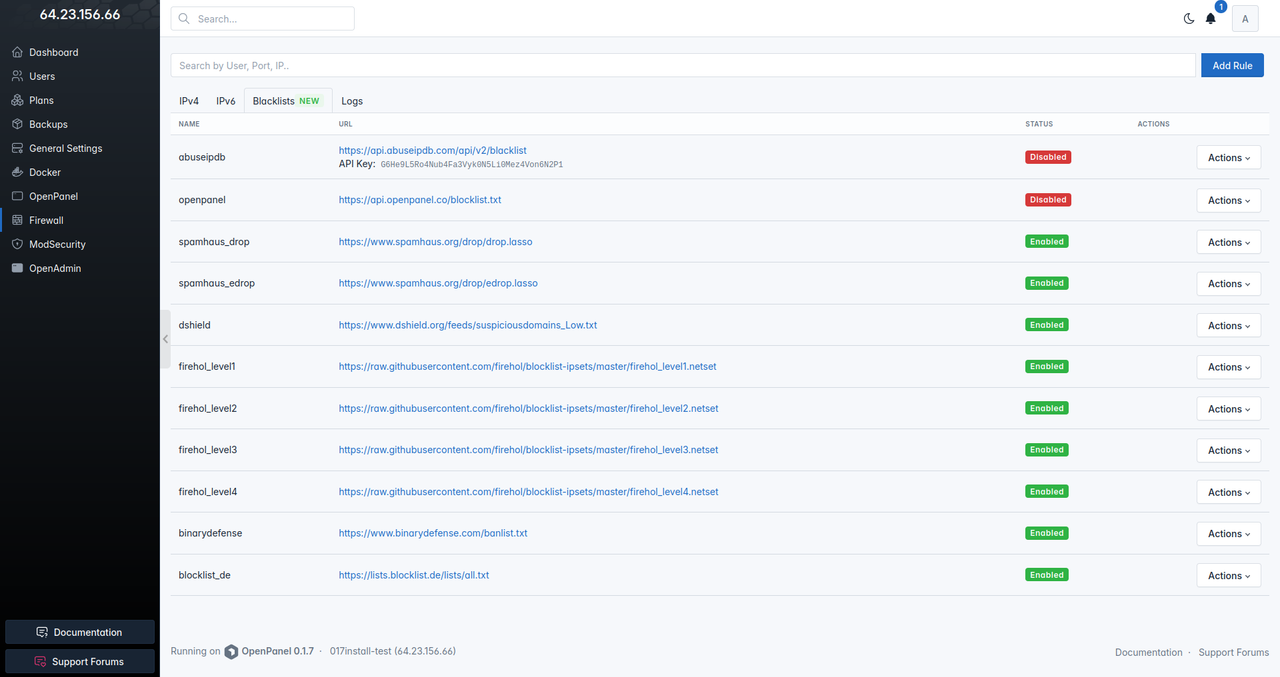
OpenAdmin Firewall now allows Administrators to easily add blacklists to block IP addresses from known malicious sources.
|
|
|
|
This feature uses the [ipset-blacklist service](https://github.com/stefanpejcic/ipset-blacklist) automating the process of fetching and blocking IPs. It's a simple yet effective way to enhance system security without manual hassle.
|
|
|
|
|
|
|
|
Default blacklists:
|
|
|
|
| Blacklist | URL |
|
|
|-----------------|----------------------------------------------------------------------|
|
|
| AbuseIPDB (DISABLED) | [https://api.abuseipdb.com/api/v2/blacklist](https://api.abuseipdb.com/api/v2/blacklist) |
|
|
| OpenPanel (DISABLED) | [https://api.openpanel.co/blocklist.txt](https://api.openpanel.co/blocklist.txt) |
|
|
| Spamhaus DROP | [https://www.spamhaus.org/drop/drop.lasso](https://www.spamhaus.org/drop/drop.lasso) |
|
|
| Spamhaus EDROP | [https://www.spamhaus.org/drop/edrop.lasso](https://www.spamhaus.org/drop/edrop.lasso) |
|
|
| DShield | [https://www.dshield.org/feeds/suspiciousdomains_Low.txt](https://www.dshield.org/feeds/suspiciousdomains_Low.txt) |
|
|
| FireHOL level1 | [https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level1.netset](https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level1.netset) |
|
|
| FireHOL level2 | [https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level2.netset](https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level2.netset) |
|
|
| FireHOL level3 | [https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level3.netset](https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level3.netset) |
|
|
| FireHOL level4 | [https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level4.netset](https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level4.netset) |
|
|
| Binary Defense | [https://www.binarydefense.com/banlist.txt](https://www.binarydefense.com/banlist.txt) |
|
|
| blocklist.de | [https://lists.blocklist.de/lists/all.txt](https://lists.blocklist.de/lists/all.txt) |
|
|
|
|
Administrators can add additional blacklists.
|
|
|
|
New opencli commands are also available:
|
|
|
|
- Download new IP addresses for all enabled blocklists:
|
|
```bash
|
|
opencli blacklist --fetch
|
|
```
|
|
- Update all ipsets rules and reload UFW service:
|
|
```bash
|
|
opencli blacklist --update_ufw
|
|
```
|
|
- Add a new blacklist:
|
|
```bash
|
|
opencli blacklist --add-blacklist name=<name> url=<url>
|
|
```
|
|
- Enable a blacklist:
|
|
```bash
|
|
opencli blacklist --enable-blacklist=<name>
|
|
```
|
|
- Disable a blacklist:
|
|
```bash
|
|
opencli blacklist --disable-blacklist=<name>
|
|
```
|
|
- Delete a blacklist:
|
|
```bash
|
|
opencli blacklist --delete-blacklist=<name>
|
|
```
|
|
|
|
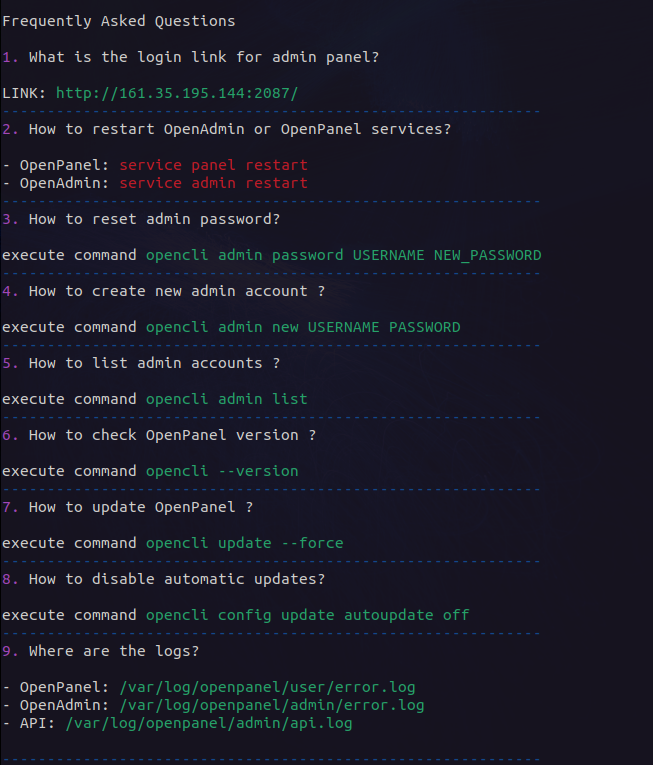
### opencli faq
|
|
|
|
OpenCLI now has a new command `opencli faq` to display most frequently asked questions:
|
|
|
|
|
|
|
|
|
|
### `/etc/openpanel/`
|
|
|
|
To enable easier updates in the future, we are gradually migrating all configuration files from `/usr/local/panel/` & `/usr/local/admin/` directories to the new `/etc/openpanel/` directory.
|
|
|
|
This will separate configuration files in /etc/ from all the code in /usr/ and therefore no configuration files will need to be moved&restored when performing updates.
|
|
|
|
Current changes include:
|
|
|
|
- Forbidden usernames file is now moved from: `/usr/local/admin/scripts/helpers/forbidden_usernames.txt` to `/etc/openpanel/openadmin/config/forbidden_usernames.txt`
|
|
- FTP configuration files are stored under `/etc/openpanel/ftp/users/`
|
|
|
|
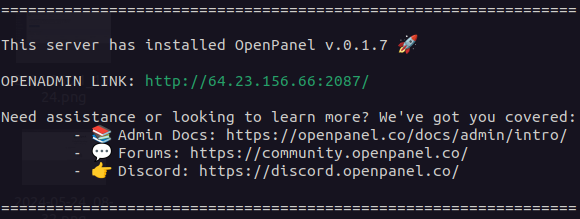
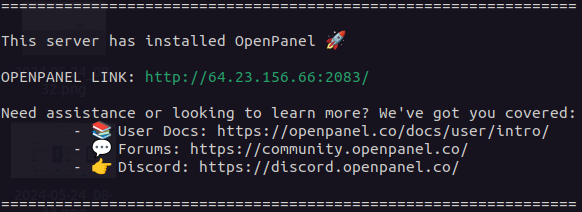
### SSH Welcome
|
|
|
|
A welcome message is shown to administrators upon logging into the server. The message currently displays OpenPanel version, admin link and help links. In the future it will also check for OpenPanel updates and display reminders.
|
|
|
|
|
|
|
|
Custom SSH welcome message is also shown to OpenPanel users upon logging into the server. This message can be customized by the Administrator.
|
|
|
|
|
|
|
|
|