mirror of
https://github.com/stefanpejcic/openpanel
synced 2025-06-26 18:28:26 +00:00
102 lines
4.6 KiB
Markdown
102 lines
4.6 KiB
Markdown
---
|
|
hide_table_of_contents: true
|
|
---
|
|
|
|
|
|
# 0.1.9
|
|
|
|
Not yet released.
|
|
|
|
|
|
### 🚀 New features
|
|
- OpenAdmin Notifications Center is now using [Sentinel](https://github.com/stefanpejcic/Sentinel/tree/main) service
|
|
- [IPset Blacklists for UFW](#ipset-blacklists)
|
|
- [OpenPanel FTP - FTP module for OpenPanel (**BETA**)](https://github.com/stefanpejcic/OpenPanel-FTP/)
|
|
- [OpenMail - Emails module for OpenPanel (**BETA**)](https://github.com/stefanpejcic/OpenMail/)
|
|
- [`opencli faq` command to show frequently asked questions](#opencli-faq)
|
|
|
|
### 🐛 Bug fixes
|
|
- Fixed bugs with `opencli admin disable` and `opencli admin enable` commands.
|
|
- Fixed bug with `opencli report` that failed to retrive MySQL version for mysql running inside docker container.
|
|
|
|
|
|
### 💅 Polish
|
|
- Working server time on OpenAdmin > Dashboard.
|
|
- CPU type information on OpenAdmin > Dashboard.
|
|
- Install script now supports optional flags `--enable_ftp` and `--enable_mail` to enable experimental features.
|
|
- `opencli -v` is now an alias for `opencli --version`.
|
|
-
|
|
|
|
|
|
## IPset Blacklists
|
|
|
|
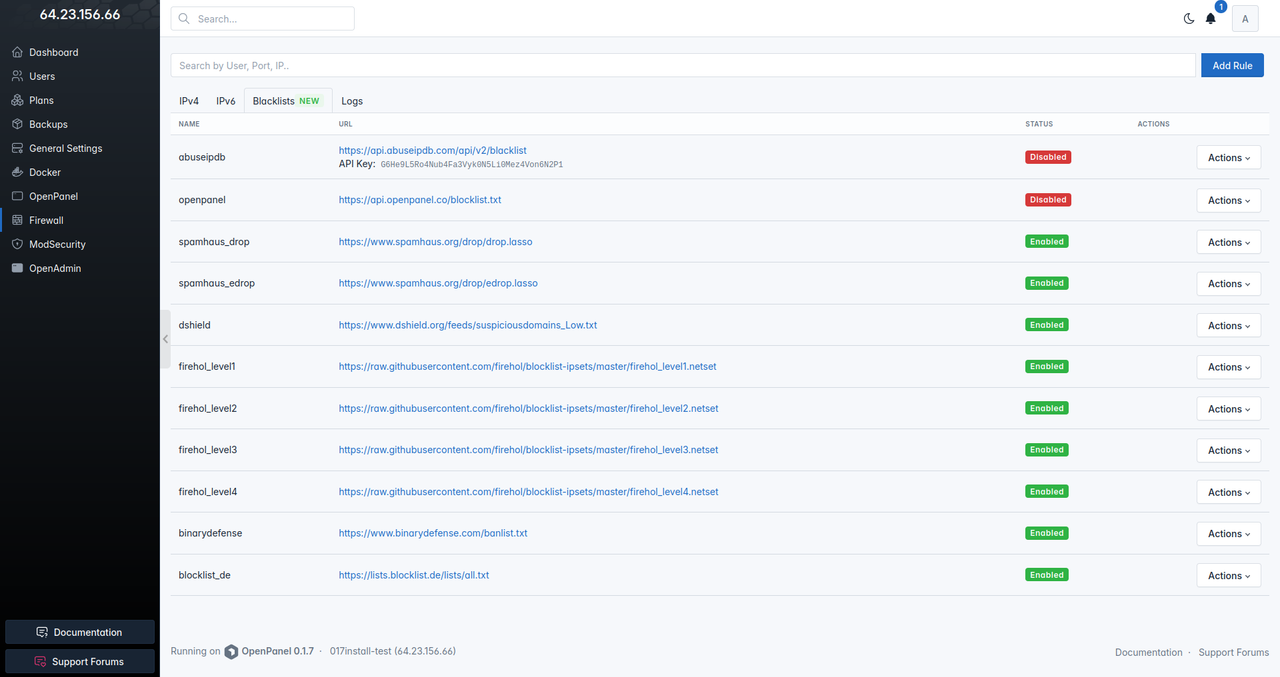
OpenAdmin Firewall now allows Administrators to easily add blacklists to block IP addresses from known malicious sources.
|
|
|
|
This feature uses the [ipset-blacklist service](https://github.com/stefanpejcic/ipset-blacklist) automating the process of fetching and blocking IPs. It's a simple yet effective way to enhance system security without manual hassle.
|
|
|
|
|
|
|
|
Default blacklists:
|
|
|
|
| Blacklist | URL |
|
|
|-----------------|----------------------------------------------------------------------|
|
|
| AbuseIPDB (DISABLED) | [https://api.abuseipdb.com/api/v2/blacklist](https://api.abuseipdb.com/api/v2/blacklist) |
|
|
| OpenPanel (DISABLED) | [https://api.openpanel.co/blocklist.txt](https://api.openpanel.co/blocklist.txt) |
|
|
| Spamhaus DROP | [https://www.spamhaus.org/drop/drop.lasso](https://www.spamhaus.org/drop/drop.lasso) |
|
|
| Spamhaus EDROP | [https://www.spamhaus.org/drop/edrop.lasso](https://www.spamhaus.org/drop/edrop.lasso) |
|
|
| DShield | [https://www.dshield.org/feeds/suspiciousdomains_Low.txt](https://www.dshield.org/feeds/suspiciousdomains_Low.txt) |
|
|
| FireHOL level1 | [https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level1.netset](https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level1.netset) |
|
|
| FireHOL level2 | [https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level2.netset](https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level2.netset) |
|
|
| FireHOL level3 | [https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level3.netset](https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level3.netset) |
|
|
| FireHOL level4 | [https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level4.netset](https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level4.netset) |
|
|
| Binary Defense | [https://www.binarydefense.com/banlist.txt](https://www.binarydefense.com/banlist.txt) |
|
|
| blocklist.de | [https://lists.blocklist.de/lists/all.txt](https://lists.blocklist.de/lists/all.txt) |
|
|
|
|
Administrators can add additional blacklists.
|
|
|
|
New opencli commands are also available:
|
|
|
|
- Download new IP addresses for all enabled blocklists:
|
|
```bash
|
|
opencli blacklist --fetch
|
|
```
|
|
- Update all ipsets rules and reload UFW service:
|
|
```bash
|
|
opencli blacklist --update_ufw
|
|
```
|
|
- Add a new blacklist:
|
|
```bash
|
|
opencli blacklist --add-blacklist name=<name> url=<url>
|
|
```
|
|
- Enable a blacklist:
|
|
```bash
|
|
opencli blacklist --enable-blacklist=<name>
|
|
```
|
|
- Disable a blacklist:
|
|
```bash
|
|
opencli blacklist --disable-blacklist=<name>
|
|
```
|
|
- Delete a blacklist:
|
|
```bash
|
|
opencli blacklist --delete-blacklist=<name>
|
|
```
|
|
|
|
### opencli faq
|
|
|
|
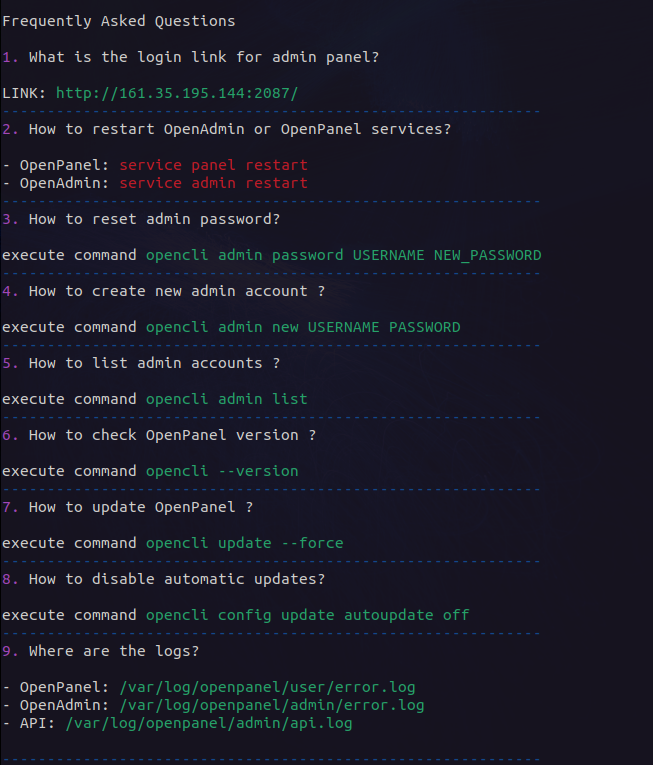
OpenCLI now has a new command `opencli faq` to display most frequently asked questions:
|
|
|
|
|
|
|
|
|
|
## `/etc/openpanel/`
|
|
|
|
To enable easier updates in the future, we are gradually migrating all configuration files from `/usr/local/panel/` & `/usr/local/admin/` directories to the new `/etc/openpanel/` directory.
|
|
|
|
This will separate configuration files in /etc/ from all the code in /usr/ and therefore no configuration files will need to be moved&restored when performing updates.
|
|
|
|
Current changes include:
|
|
|
|
- Forbidden usernames file is now moved from: `/usr/local/admin/scripts/helpers/forbidden_usernames.txt` to `/etc/openpanel/openadmin/config/forbidden_usernames.txt`
|
|
- FTP configuration files are stored under `/etc/openpanel/ftp/users/`
|
|
-
|