test version
This commit is contained in:
3
.gitignore
vendored
Normal file
3
.gitignore
vendored
Normal file
@@ -0,0 +1,3 @@
|
||||
./tor/*
|
||||
./*.sh
|
||||
|
||||
92
Dockerfile
Normal file
92
Dockerfile
Normal file
@@ -0,0 +1,92 @@
|
||||
#
|
||||
# Dockerfile for the Private Tor Network
|
||||
#
|
||||
# This is a dockerfile to build a Debian host and
|
||||
# compile a version of tor from the Tor apt repos.
|
||||
# NOTE: This is a modification of chriswayg's solid
|
||||
# base.
|
||||
#
|
||||
# Usage:
|
||||
# This works best using a docker compose command so you can run the
|
||||
# necessary other servers for it to talk to. But if you want o run
|
||||
# manually:
|
||||
#
|
||||
# docker run --rm -it -e ROLE=DA antitree/tor-server /bin/bash
|
||||
|
||||
FROM debian:latest
|
||||
MAINTAINER Antitree antitree@protonmail.com
|
||||
|
||||
# Sets which version of tor to use. See the Tor Projects git page for available tags
|
||||
# Examples:
|
||||
# * tor-0.2.8.4-rc
|
||||
# * tor-0.2.7.6
|
||||
# * tor-0.2.7.5
|
||||
# * release-0.2.1
|
||||
ENV TOR_VER="tor-0.4.8.12"
|
||||
#ENV TOR_VER="master"
|
||||
# NOTE sometimes the master branch doesn't compile so I'm sticking with the release
|
||||
# feel free to change this to master to get the latest and greatest
|
||||
|
||||
# Sets the nickname if you didn't set one, default ports, and the path
|
||||
# where to mount the key material used by the clients.
|
||||
ENV TERM=xterm \
|
||||
TOR_ORPORT=9001 \
|
||||
TOR_DIRPORT=9030 \
|
||||
TOR_DIR=/tor
|
||||
|
||||
|
||||
ARG NICKNAME
|
||||
ENV NICKNAME $NICKNAME
|
||||
|
||||
# Install build dependencies
|
||||
RUN apt-get update && \
|
||||
build_temps="build-essential automake" && \
|
||||
build_deps="libssl-dev zlib1g-dev libevent-dev ca-certificates\
|
||||
dh-apparmor libseccomp-dev \
|
||||
git" && \
|
||||
DEBIAN_FRONTEND=noninteractive apt-get -y --no-install-recommends install $build_deps $build_temps \
|
||||
init-system-helpers \
|
||||
pwgen && \
|
||||
mkdir /src && \
|
||||
apt-get update && \
|
||||
apt-get install -y tor iproute2 && \
|
||||
apt-get install -y gettext && \
|
||||
cd /src && \
|
||||
git clone https://git.torproject.org/tor.git && \
|
||||
cd tor && \
|
||||
git checkout ${TOR_VER} && \
|
||||
./autogen.sh && \
|
||||
./configure --disable-asciidoc && \
|
||||
make && \
|
||||
make install && \
|
||||
apt-get -y purge --auto-remove $build_temps && \
|
||||
apt-get clean && rm -r /var/lib/apt/lists/* && \
|
||||
rm -rf /src/*
|
||||
|
||||
# Copy the base tor configuration file
|
||||
COPY ./config/torrc* /etc/tor/
|
||||
|
||||
# Copy docker-entrypoint and the fingerprint script
|
||||
COPY ./scripts/ /usr/local/bin/
|
||||
|
||||
|
||||
# Persist data (Usually don't want this)
|
||||
#VOLUME /etc/tor /var/lib/tor
|
||||
|
||||
# Create the shared directory
|
||||
RUN mkdir -p ${TOR_DIR}
|
||||
|
||||
# Копирование шаблона конфигурации
|
||||
COPY torrc.da.template /etc/tor/torrc.da.template
|
||||
|
||||
# Использование `envsubst` для замены переменных в шаблоне и создания файла torrc
|
||||
RUN envsubst < /etc/tor/torrc.da.template > /etc/tor/torrc.da
|
||||
|
||||
# ORPort, DirPort, ObfsproxyPort
|
||||
# TODO make these match the env variables
|
||||
# TODO is this necessary anymore?
|
||||
EXPOSE 9001 9030 9051
|
||||
|
||||
ENTRYPOINT ["docker-entrypoint"]
|
||||
|
||||
CMD ["tor", "-f", "/etc/tor/torrc"]
|
||||
340
LICENSE
Normal file
340
LICENSE
Normal file
@@ -0,0 +1,340 @@
|
||||
GNU GENERAL PUBLIC LICENSE
|
||||
Version 2, June 1991
|
||||
|
||||
Copyright (C) 1989, 1991 Free Software Foundation, Inc., <http://fsf.org/>
|
||||
51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA
|
||||
Everyone is permitted to copy and distribute verbatim copies
|
||||
of this license document, but changing it is not allowed.
|
||||
|
||||
Preamble
|
||||
|
||||
The licenses for most software are designed to take away your
|
||||
freedom to share and change it. By contrast, the GNU General Public
|
||||
License is intended to guarantee your freedom to share and change free
|
||||
software--to make sure the software is free for all its users. This
|
||||
General Public License applies to most of the Free Software
|
||||
Foundation's software and to any other program whose authors commit to
|
||||
using it. (Some other Free Software Foundation software is covered by
|
||||
the GNU Lesser General Public License instead.) You can apply it to
|
||||
your programs, too.
|
||||
|
||||
When we speak of free software, we are referring to freedom, not
|
||||
price. Our General Public Licenses are designed to make sure that you
|
||||
have the freedom to distribute copies of free software (and charge for
|
||||
this service if you wish), that you receive source code or can get it
|
||||
if you want it, that you can change the software or use pieces of it
|
||||
in new free programs; and that you know you can do these things.
|
||||
|
||||
To protect your rights, we need to make restrictions that forbid
|
||||
anyone to deny you these rights or to ask you to surrender the rights.
|
||||
These restrictions translate to certain responsibilities for you if you
|
||||
distribute copies of the software, or if you modify it.
|
||||
|
||||
For example, if you distribute copies of such a program, whether
|
||||
gratis or for a fee, you must give the recipients all the rights that
|
||||
you have. You must make sure that they, too, receive or can get the
|
||||
source code. And you must show them these terms so they know their
|
||||
rights.
|
||||
|
||||
We protect your rights with two steps: (1) copyright the software, and
|
||||
(2) offer you this license which gives you legal permission to copy,
|
||||
distribute and/or modify the software.
|
||||
|
||||
Also, for each author's protection and ours, we want to make certain
|
||||
that everyone understands that there is no warranty for this free
|
||||
software. If the software is modified by someone else and passed on, we
|
||||
want its recipients to know that what they have is not the original, so
|
||||
that any problems introduced by others will not reflect on the original
|
||||
authors' reputations.
|
||||
|
||||
Finally, any free program is threatened constantly by software
|
||||
patents. We wish to avoid the danger that redistributors of a free
|
||||
program will individually obtain patent licenses, in effect making the
|
||||
program proprietary. To prevent this, we have made it clear that any
|
||||
patent must be licensed for everyone's free use or not licensed at all.
|
||||
|
||||
The precise terms and conditions for copying, distribution and
|
||||
modification follow.
|
||||
|
||||
GNU GENERAL PUBLIC LICENSE
|
||||
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
|
||||
|
||||
0. This License applies to any program or other work which contains
|
||||
a notice placed by the copyright holder saying it may be distributed
|
||||
under the terms of this General Public License. The "Program", below,
|
||||
refers to any such program or work, and a "work based on the Program"
|
||||
means either the Program or any derivative work under copyright law:
|
||||
that is to say, a work containing the Program or a portion of it,
|
||||
either verbatim or with modifications and/or translated into another
|
||||
language. (Hereinafter, translation is included without limitation in
|
||||
the term "modification".) Each licensee is addressed as "you".
|
||||
|
||||
Activities other than copying, distribution and modification are not
|
||||
covered by this License; they are outside its scope. The act of
|
||||
running the Program is not restricted, and the output from the Program
|
||||
is covered only if its contents constitute a work based on the
|
||||
Program (independent of having been made by running the Program).
|
||||
Whether that is true depends on what the Program does.
|
||||
|
||||
1. You may copy and distribute verbatim copies of the Program's
|
||||
source code as you receive it, in any medium, provided that you
|
||||
conspicuously and appropriately publish on each copy an appropriate
|
||||
copyright notice and disclaimer of warranty; keep intact all the
|
||||
notices that refer to this License and to the absence of any warranty;
|
||||
and give any other recipients of the Program a copy of this License
|
||||
along with the Program.
|
||||
|
||||
You may charge a fee for the physical act of transferring a copy, and
|
||||
you may at your option offer warranty protection in exchange for a fee.
|
||||
|
||||
2. You may modify your copy or copies of the Program or any portion
|
||||
of it, thus forming a work based on the Program, and copy and
|
||||
distribute such modifications or work under the terms of Section 1
|
||||
above, provided that you also meet all of these conditions:
|
||||
|
||||
a) You must cause the modified files to carry prominent notices
|
||||
stating that you changed the files and the date of any change.
|
||||
|
||||
b) You must cause any work that you distribute or publish, that in
|
||||
whole or in part contains or is derived from the Program or any
|
||||
part thereof, to be licensed as a whole at no charge to all third
|
||||
parties under the terms of this License.
|
||||
|
||||
c) If the modified program normally reads commands interactively
|
||||
when run, you must cause it, when started running for such
|
||||
interactive use in the most ordinary way, to print or display an
|
||||
announcement including an appropriate copyright notice and a
|
||||
notice that there is no warranty (or else, saying that you provide
|
||||
a warranty) and that users may redistribute the program under
|
||||
these conditions, and telling the user how to view a copy of this
|
||||
License. (Exception: if the Program itself is interactive but
|
||||
does not normally print such an announcement, your work based on
|
||||
the Program is not required to print an announcement.)
|
||||
|
||||
These requirements apply to the modified work as a whole. If
|
||||
identifiable sections of that work are not derived from the Program,
|
||||
and can be reasonably considered independent and separate works in
|
||||
themselves, then this License, and its terms, do not apply to those
|
||||
sections when you distribute them as separate works. But when you
|
||||
distribute the same sections as part of a whole which is a work based
|
||||
on the Program, the distribution of the whole must be on the terms of
|
||||
this License, whose permissions for other licensees extend to the
|
||||
entire whole, and thus to each and every part regardless of who wrote it.
|
||||
|
||||
Thus, it is not the intent of this section to claim rights or contest
|
||||
your rights to work written entirely by you; rather, the intent is to
|
||||
exercise the right to control the distribution of derivative or
|
||||
collective works based on the Program.
|
||||
|
||||
In addition, mere aggregation of another work not based on the Program
|
||||
with the Program (or with a work based on the Program) on a volume of
|
||||
a storage or distribution medium does not bring the other work under
|
||||
the scope of this License.
|
||||
|
||||
3. You may copy and distribute the Program (or a work based on it,
|
||||
under Section 2) in object code or executable form under the terms of
|
||||
Sections 1 and 2 above provided that you also do one of the following:
|
||||
|
||||
a) Accompany it with the complete corresponding machine-readable
|
||||
source code, which must be distributed under the terms of Sections
|
||||
1 and 2 above on a medium customarily used for software interchange; or,
|
||||
|
||||
b) Accompany it with a written offer, valid for at least three
|
||||
years, to give any third party, for a charge no more than your
|
||||
cost of physically performing source distribution, a complete
|
||||
machine-readable copy of the corresponding source code, to be
|
||||
distributed under the terms of Sections 1 and 2 above on a medium
|
||||
customarily used for software interchange; or,
|
||||
|
||||
c) Accompany it with the information you received as to the offer
|
||||
to distribute corresponding source code. (This alternative is
|
||||
allowed only for noncommercial distribution and only if you
|
||||
received the program in object code or executable form with such
|
||||
an offer, in accord with Subsection b above.)
|
||||
|
||||
The source code for a work means the preferred form of the work for
|
||||
making modifications to it. For an executable work, complete source
|
||||
code means all the source code for all modules it contains, plus any
|
||||
associated interface definition files, plus the scripts used to
|
||||
control compilation and installation of the executable. However, as a
|
||||
special exception, the source code distributed need not include
|
||||
anything that is normally distributed (in either source or binary
|
||||
form) with the major components (compiler, kernel, and so on) of the
|
||||
operating system on which the executable runs, unless that component
|
||||
itself accompanies the executable.
|
||||
|
||||
If distribution of executable or object code is made by offering
|
||||
access to copy from a designated place, then offering equivalent
|
||||
access to copy the source code from the same place counts as
|
||||
distribution of the source code, even though third parties are not
|
||||
compelled to copy the source along with the object code.
|
||||
|
||||
4. You may not copy, modify, sublicense, or distribute the Program
|
||||
except as expressly provided under this License. Any attempt
|
||||
otherwise to copy, modify, sublicense or distribute the Program is
|
||||
void, and will automatically terminate your rights under this License.
|
||||
However, parties who have received copies, or rights, from you under
|
||||
this License will not have their licenses terminated so long as such
|
||||
parties remain in full compliance.
|
||||
|
||||
5. You are not required to accept this License, since you have not
|
||||
signed it. However, nothing else grants you permission to modify or
|
||||
distribute the Program or its derivative works. These actions are
|
||||
prohibited by law if you do not accept this License. Therefore, by
|
||||
modifying or distributing the Program (or any work based on the
|
||||
Program), you indicate your acceptance of this License to do so, and
|
||||
all its terms and conditions for copying, distributing or modifying
|
||||
the Program or works based on it.
|
||||
|
||||
6. Each time you redistribute the Program (or any work based on the
|
||||
Program), the recipient automatically receives a license from the
|
||||
original licensor to copy, distribute or modify the Program subject to
|
||||
these terms and conditions. You may not impose any further
|
||||
restrictions on the recipients' exercise of the rights granted herein.
|
||||
You are not responsible for enforcing compliance by third parties to
|
||||
this License.
|
||||
|
||||
7. If, as a consequence of a court judgment or allegation of patent
|
||||
infringement or for any other reason (not limited to patent issues),
|
||||
conditions are imposed on you (whether by court order, agreement or
|
||||
otherwise) that contradict the conditions of this License, they do not
|
||||
excuse you from the conditions of this License. If you cannot
|
||||
distribute so as to satisfy simultaneously your obligations under this
|
||||
License and any other pertinent obligations, then as a consequence you
|
||||
may not distribute the Program at all. For example, if a patent
|
||||
license would not permit royalty-free redistribution of the Program by
|
||||
all those who receive copies directly or indirectly through you, then
|
||||
the only way you could satisfy both it and this License would be to
|
||||
refrain entirely from distribution of the Program.
|
||||
|
||||
If any portion of this section is held invalid or unenforceable under
|
||||
any particular circumstance, the balance of the section is intended to
|
||||
apply and the section as a whole is intended to apply in other
|
||||
circumstances.
|
||||
|
||||
It is not the purpose of this section to induce you to infringe any
|
||||
patents or other property right claims or to contest validity of any
|
||||
such claims; this section has the sole purpose of protecting the
|
||||
integrity of the free software distribution system, which is
|
||||
implemented by public license practices. Many people have made
|
||||
generous contributions to the wide range of software distributed
|
||||
through that system in reliance on consistent application of that
|
||||
system; it is up to the author/donor to decide if he or she is willing
|
||||
to distribute software through any other system and a licensee cannot
|
||||
impose that choice.
|
||||
|
||||
This section is intended to make thoroughly clear what is believed to
|
||||
be a consequence of the rest of this License.
|
||||
|
||||
8. If the distribution and/or use of the Program is restricted in
|
||||
certain countries either by patents or by copyrighted interfaces, the
|
||||
original copyright holder who places the Program under this License
|
||||
may add an explicit geographical distribution limitation excluding
|
||||
those countries, so that distribution is permitted only in or among
|
||||
countries not thus excluded. In such case, this License incorporates
|
||||
the limitation as if written in the body of this License.
|
||||
|
||||
9. The Free Software Foundation may publish revised and/or new versions
|
||||
of the General Public License from time to time. Such new versions will
|
||||
be similar in spirit to the present version, but may differ in detail to
|
||||
address new problems or concerns.
|
||||
|
||||
Each version is given a distinguishing version number. If the Program
|
||||
specifies a version number of this License which applies to it and "any
|
||||
later version", you have the option of following the terms and conditions
|
||||
either of that version or of any later version published by the Free
|
||||
Software Foundation. If the Program does not specify a version number of
|
||||
this License, you may choose any version ever published by the Free Software
|
||||
Foundation.
|
||||
|
||||
10. If you wish to incorporate parts of the Program into other free
|
||||
programs whose distribution conditions are different, write to the author
|
||||
to ask for permission. For software which is copyrighted by the Free
|
||||
Software Foundation, write to the Free Software Foundation; we sometimes
|
||||
make exceptions for this. Our decision will be guided by the two goals
|
||||
of preserving the free status of all derivatives of our free software and
|
||||
of promoting the sharing and reuse of software generally.
|
||||
|
||||
NO WARRANTY
|
||||
|
||||
11. BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY
|
||||
FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN
|
||||
OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES
|
||||
PROVIDE THE PROGRAM "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED
|
||||
OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
|
||||
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE ENTIRE RISK AS
|
||||
TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE
|
||||
PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING,
|
||||
REPAIR OR CORRECTION.
|
||||
|
||||
12. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING
|
||||
WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR
|
||||
REDISTRIBUTE THE PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES,
|
||||
INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING
|
||||
OUT OF THE USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED
|
||||
TO LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY
|
||||
YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER
|
||||
PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE
|
||||
POSSIBILITY OF SUCH DAMAGES.
|
||||
|
||||
END OF TERMS AND CONDITIONS
|
||||
|
||||
How to Apply These Terms to Your New Programs
|
||||
|
||||
If you develop a new program, and you want it to be of the greatest
|
||||
possible use to the public, the best way to achieve this is to make it
|
||||
free software which everyone can redistribute and change under these terms.
|
||||
|
||||
To do so, attach the following notices to the program. It is safest
|
||||
to attach them to the start of each source file to most effectively
|
||||
convey the exclusion of warranty; and each file should have at least
|
||||
the "copyright" line and a pointer to where the full notice is found.
|
||||
|
||||
{description}
|
||||
Copyright (C) {year} {fullname}
|
||||
|
||||
This program is free software; you can redistribute it and/or modify
|
||||
it under the terms of the GNU General Public License as published by
|
||||
the Free Software Foundation; either version 2 of the License, or
|
||||
(at your option) any later version.
|
||||
|
||||
This program is distributed in the hope that it will be useful,
|
||||
but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||
GNU General Public License for more details.
|
||||
|
||||
You should have received a copy of the GNU General Public License along
|
||||
with this program; if not, write to the Free Software Foundation, Inc.,
|
||||
51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
|
||||
|
||||
Also add information on how to contact you by electronic and paper mail.
|
||||
|
||||
If the program is interactive, make it output a short notice like this
|
||||
when it starts in an interactive mode:
|
||||
|
||||
Gnomovision version 69, Copyright (C) year name of author
|
||||
Gnomovision comes with ABSOLUTELY NO WARRANTY; for details type `show w'.
|
||||
This is free software, and you are welcome to redistribute it
|
||||
under certain conditions; type `show c' for details.
|
||||
|
||||
The hypothetical commands `show w' and `show c' should show the appropriate
|
||||
parts of the General Public License. Of course, the commands you use may
|
||||
be called something other than `show w' and `show c'; they could even be
|
||||
mouse-clicks or menu items--whatever suits your program.
|
||||
|
||||
You should also get your employer (if you work as a programmer) or your
|
||||
school, if any, to sign a "copyright disclaimer" for the program, if
|
||||
necessary. Here is a sample; alter the names:
|
||||
|
||||
Yoyodyne, Inc., hereby disclaims all copyright interest in the program
|
||||
`Gnomovision' (which makes passes at compilers) written by James Hacker.
|
||||
|
||||
{signature of Ty Coon}, 1 April 1989
|
||||
Ty Coon, President of Vice
|
||||
|
||||
This General Public License does not permit incorporating your program into
|
||||
proprietary programs. If your program is a subroutine library, you may
|
||||
consider it more useful to permit linking proprietary applications with the
|
||||
library. If this is what you want to do, use the GNU Lesser General
|
||||
Public License instead of this License.
|
||||
|
||||
174
README.md
Normal file
174
README.md
Normal file
@@ -0,0 +1,174 @@
|
||||
## Private Tor Network on Docker
|
||||
|
||||
##### An isolated, private tor network running entirely in Docker containers
|
||||
|
||||
### Quickstart
|
||||
|
||||
The easiest way to get a tor network up and running is to use the docker-compose create and then scale function
|
||||
|
||||
```
|
||||
docker-compose up
|
||||
docker-compose scale relay=5 exit=3
|
||||
```
|
||||
|
||||
This will create 3 directory authorities (DA's), 1 client listning on port 9050, 5 relays, and 3 exits. You can scale to whatever you want.
|
||||
|
||||
### Uses
|
||||
|
||||
If you're going "Why do I want this?" here's a few examples:
|
||||
|
||||
**tor research**: learn how tor interacts with nodes, make modifications to settings and see what happens, understand how the Tor Network operates without affecting real people. Originally this project was part of a class I wrote to teach about how tor works.
|
||||
|
||||
**tor development**: in the case you're working on a patch that is more complex and requires seeing what happens on the tor network, you can apply the patches to the containers.
|
||||
|
||||
**traffic analysis**: Test out the latest tor exploit and pretend to be a nation state adversary.
|
||||
|
||||
*If this needs to be said, this should never be used as a replacement for tor. This is for research purposes alone.*
|
||||
|
||||
### Storage & Tor Network Configuration
|
||||
|
||||
All of the required information that other nodes need to know about on the network are stored in a named volume `torvol` which you can find the path for doing `docker volume inspect privatetornetwork_torvol` or use `docker volume ls` to find its name on your system.
|
||||
|
||||
If you are running multiple instances or are rebuilding it, make sure you delete this named volume or you'll accidentally use a previous iteration's keys. Easiest way is:
|
||||
|
||||
~~~
|
||||
docker-compose rm
|
||||
docker volume rm privatetornetwork_torvol
|
||||
~~~
|
||||
|
||||
### Running Individual Roles
|
||||
|
||||
You can manually build a tor network if you don't want to use docker-compose but you'll need to make sure you pass the correct DA fingerprints to each of the servers. Also make sure you create a user defined interface so that it doesn't try to use the default bridge. For example, this would make the first directory authority (DA)
|
||||
`docker run -e ROLE=DA --network tornet antitree/private-tor`
|
||||
|
||||
Or setup a relay:
|
||||
`docker run -e ROLE=RELAY --network tornet antitree/private-tor`
|
||||
|
||||
Watching the logs on a relay
|
||||
`docker logs -f {name of your container}`
|
||||
|
||||
Available roles right now are:
|
||||
|
||||
* DA - directory authority
|
||||
* RELAY - non-exit relay
|
||||
* EXIT - exit relay
|
||||
* CLIENT - exposes the tor socks port on 9050 to the host
|
||||
|
||||
### Versions
|
||||
You can run a variety of the most common tor versions by changing the image name from "antitree/private-tor:latest" to something like "antitree/private-tor:0.3.2". Current tags supported are from 0.2.6 to 0.3.5.
|
||||
|
||||
If you'd like to try a very specific version you can rebuild the Dockerfile and edit the ["TOR_VER"](https://github.com/antitree/private-tor-network/blob/master/Dockerfile#L25) environment variable. These values should match the [branch names](https://gitweb.torproject.org/tor.git/refs/heads) from the official tor repo.
|
||||
|
||||
|
||||
### Onion Services
|
||||
|
||||
If you'd like to run an onion service, you can use the `TOR_HS_PORT` and `TOR_HS_ADDRESS` environment variables. By default, there is a hidden service setup in the docker-compose.yml file.
|
||||
|
||||
Example configuration that will run an onion service named "hs" and a web server named "web". This will link the web service to the onion service so that "hs" will forward connections to "web" on port 80. This is done using the `links` configuration feature for docker-compose.
|
||||
|
||||
```
|
||||
hs:
|
||||
image: antitree/private-tor
|
||||
expose:
|
||||
- "80"
|
||||
environment:
|
||||
ROLE: HS
|
||||
# This will create a hidden service that points to
|
||||
# the service "web" which is runing nginx. You can
|
||||
# change this to whatever ip or hostname you want
|
||||
TOR_HS_PORT: "80"
|
||||
TOR_HS_ADDR: "web"
|
||||
volumes:
|
||||
- ./tor:/tor
|
||||
depends_on:
|
||||
- da1
|
||||
- da2
|
||||
- da3
|
||||
links:
|
||||
- web
|
||||
web:
|
||||
image: nginx
|
||||
expose:
|
||||
- "80"
|
||||
```
|
||||
|
||||
NOTE: By default, this just displays the nginx start page so you may want to replace the image with a more interesting one or configure the nginx container with some static HTML to host.
|
||||
|
||||
### Tor configuration
|
||||
|
||||
This configuration is based on the Tor documentation for how to run a private tor network. You should also check out [Chutney](https://gitweb.torproject.org/chutney.git/) which does something similar with separate processes instead of containers. If you need to make a modification (such as changing the timing of the DA's) edit the `config/torrc` and/or `config/torrc.da` files. You may need to modify the Dockerfile as well.
|
||||
|
||||
### Environment variables
|
||||
|
||||
The container is built off of [chriswayg/tor-server](https://github.com/chriswayg/tor-server) but has been heavily modified to support some other env variables that you can pass to it:
|
||||
|
||||
* TOR_ORPORT - default is 7000
|
||||
* TOR_DIRPORT - default is 9030
|
||||
* TOR_DIR - container path to mount a persistent tor material. default is /tor
|
||||
* TOR_CONTROL_PWD - set the control port password to something besides "password"
|
||||
* TOR_HS_PORT - port to listen for an onion service on
|
||||
* TOR_HS_ADDR - IP or hostname of service you want to point an onion service to
|
||||
|
||||
### Things to try
|
||||
|
||||
The `/util/` directory contains a few scripts to play with one the host computer. Once you have a
|
||||
private tor network up and running you can try out some of the tools in there.
|
||||
|
||||
**Using Arm**:
|
||||
|
||||
With the tor control port exposed to the host, you can use arm to monitor the client.
|
||||
```
|
||||
apt-get install tor-arm
|
||||
arm
|
||||
```
|
||||
NOTE: There is a password to protect the control port right now. Enter "password" when prompted
|
||||
|
||||
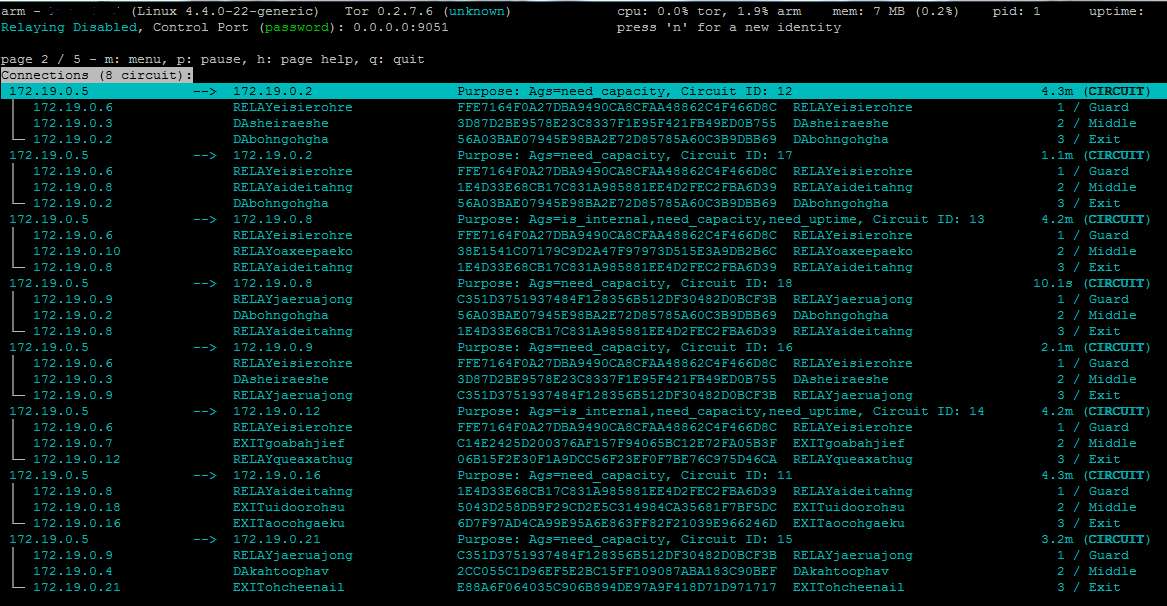
|
||||
|
||||
You can also connect arm to one of the containers if you know it's ip. You can find the IPs by running the
|
||||
`get_consensus.py` script provided or however otherway you feel like.
|
||||
|
||||
```arm -i 172.19.0.3:9051```
|
||||
|
||||
**Get Consensus**:
|
||||
|
||||
```python util/get_consensus.py```
|
||||
|
||||
This will connect to the CLIENT docker container via the tor Control Port and download the consensus which
|
||||
contains the nicknames and IPs of the relays on the network. (If this is blank, you may have to wait 30s
|
||||
while they decided on a consensus.)
|
||||
|
||||
**Tor-prompt**:
|
||||
|
||||
If you've installed arm you will probably also have the `tor-prompt` command. You can use it to manually
|
||||
gather information about some of the containers that have their Control Port exposed like so:
|
||||
|
||||
```
|
||||
tor-prompt -i {ip_of_ontainer}:9051
|
||||
Control Port password: password
|
||||
```
|
||||
|
||||
|
||||
### Debugging
|
||||
|
||||
Here are a few things to try if you're runing into issues:
|
||||
|
||||
* Check the tor logs sent to stdout `docker logs -f torserver_da_1`
|
||||
* Check all the logs with `docker-compose logs`
|
||||
* Enable verbose logging by changing the `./config/torrc`
|
||||
* Check permissions for your ./tor folder
|
||||
* Delete the files in your ./tor folder so you can start from scratch (or specifically the torrc.da file)
|
||||
* To cleanup the environment and start over you can use `docker-compose kill` and `docker-compose rm -ra` to remove them all.
|
||||
|
||||
### TODO
|
||||
|
||||
* Wait for someone to yell at me about using scale like this and then move to the new networking
|
||||
|
||||
### Dislaimer
|
||||
|
||||
This project is in no way associated with the Tor Project or their developers. Like many people I'm a fan of Tor and recommend considering ways you can help the project. Consider running a relay, donating, or writing code.
|
||||
|
||||
### Resources
|
||||
- https://github.com/andrewmichaelsmith/private-tor-network-kube Used some of this work to port to a kubernetes config
|
||||
- https://github.com/chriswayg/tor-server
|
||||
- https://www.torproject.org/docs/tor-relay-debian.html.en
|
||||
42
config/1torrc.da
Normal file
42
config/1torrc.da
Normal file
@@ -0,0 +1,42 @@
|
||||
AuthoritativeDirectory 1
|
||||
V3AuthoritativeDirectory 1
|
||||
|
||||
# Speed up the consensus cycle as fast as it will go
|
||||
# Voting Interval can be:
|
||||
# 10, 12, 15, 18, 20, 24, 25, 30, 36, 40, 45, 50, 60, ...
|
||||
# Testing Initial Voting Interval can be:
|
||||
# 5, 6, 8, 9, or any of the possible values for Voting Interval,
|
||||
# as they both need to evenly divide 30 minutes.
|
||||
# If clock desynchronisation is an issue, use an interval of at least:
|
||||
# 18 * drift in seconds, to allow for a clock slop factor
|
||||
TestingV3AuthInitialVotingInterval 300
|
||||
#V3AuthVotingInterval 15
|
||||
# VoteDelay + DistDelay must be less than VotingInterval
|
||||
TestingV3AuthInitialVoteDelay 5
|
||||
V3AuthVoteDelay 5
|
||||
TestingV3AuthInitialDistDelay 5
|
||||
V3AuthDistDelay 5
|
||||
# This is autoconfigured by chutney, so you probably don't want to use it
|
||||
#TestingV3AuthVotingStartOffset 0
|
||||
|
||||
# Work around situations where the Exit, Guard and HSDir flags aren't being set
|
||||
# These flags are all set eventually, but it takes Guard up to ~30 minutes
|
||||
# We could be more precise here, but it's easiest just to vote everything
|
||||
# Clients are sensible enough to filter out Exits without any exit ports,
|
||||
# and Guards and HSDirs without ORPorts
|
||||
# If your tor doesn't recognise TestingDirAuthVoteExit/HSDir,
|
||||
# either update your chutney to a 2015 version,
|
||||
# or update your tor to a later version, most likely 0.2.6.2-final
|
||||
|
||||
# These are all set in common.i in the Comprehensive/Rapid sections
|
||||
# Work around Exit requirements
|
||||
#TestingDirAuthVoteExit *
|
||||
# Work around bandwidth thresholds for exits
|
||||
#TestingMinExitFlagThreshold 0
|
||||
# Work around Guard uptime requirements
|
||||
#TestingDirAuthVoteGuard *
|
||||
# Work around HSDir uptime and ORPort connectivity requirements
|
||||
#TestingDirAuthVoteHSDir *
|
||||
|
||||
Address 127.0.0.1
|
||||
DirAuthority Alex 127.0.0.1:9030 7EB85B97333C276E7D88000F074DFCD534CE69E2
|
||||
48
config/new_torrc.da
Normal file
48
config/new_torrc.da
Normal file
@@ -0,0 +1,48 @@
|
||||
AuthoritativeDirectory 1
|
||||
V3AuthoritativeDirectory 1
|
||||
|
||||
# Speed up the consensus cycle as fast as it will go
|
||||
# Voting Interval can be:
|
||||
# 10, 12, 15, 18, 20, 24, 25, 30, 36, 40, 45, 50, 60, ...
|
||||
# Testing Initial Voting Interval can be:
|
||||
# 5, 6, 8, 9, or any of the possible values for Voting Interval,
|
||||
# as they both need to evenly divide 30 minutes.
|
||||
# If clock desynchronisation is an issue, use an interval of at least:
|
||||
# 18 * drift in seconds, to allow for a clock slop factor
|
||||
TestingV3AuthInitialVotingInterval 300
|
||||
#V3AuthVotingInterval 15
|
||||
# VoteDelay + DistDelay must be less than VotingInterval
|
||||
TestingV3AuthInitialVoteDelay 5
|
||||
V3AuthVoteDelay 5
|
||||
TestingV3AuthInitialDistDelay 5
|
||||
V3AuthDistDelay 5
|
||||
# This is autoconfigured by chutney, so you probably don't want to use it
|
||||
#TestingV3AuthVotingStartOffset 0
|
||||
|
||||
# Work around situations where the Exit, Guard and HSDir flags aren't being set
|
||||
# These flags are all set eventually, but it takes Guard up to ~30 minutes
|
||||
# We could be more precise here, but it's easiest just to vote everything
|
||||
# Clients are sensible enough to filter out Exits without any exit ports,
|
||||
# and Guards and HSDirs without ORPorts
|
||||
# If your tor doesn't recognise TestingDirAuthVoteExit/HSDir,
|
||||
# either update your chutney to a 2015 version,
|
||||
# or update your tor to a later version, most likely 0.2.6.2-final
|
||||
|
||||
# These are all set in common.i in the Comprehensive/Rapid sections
|
||||
# Work around Exit requirements
|
||||
#TestingDirAuthVoteExit *
|
||||
# Work around bandwidth thresholds for exits
|
||||
#TestingMinExitFlagThreshold 0
|
||||
# Work around Guard uptime requirements
|
||||
#TestingDirAuthVoteGuard *
|
||||
# Work around HSDir uptime and ORPort connectivity requirements
|
||||
#TestingDirAuthVoteHSDir *
|
||||
|
||||
|
||||
DirAuthority Alex 127.0.0.1:9030 7EB85B97333C276E7D88000F074DFCD534CE69E2
|
||||
#v3ident=b80992426b37f9ad9e2335ee1c26239da838d4c7
|
||||
|
||||
ContactInfo Alex Voronkov
|
||||
# Address 89.129.190.248
|
||||
|
||||
Address 127.0.0.1:9030
|
||||
2
config/tor-apt-sources.list
Normal file
2
config/tor-apt-sources.list
Normal file
@@ -0,0 +1,2 @@
|
||||
deb http://deb.torproject.org/torproject.org latest main
|
||||
deb-src http://deb.torproject.org/torproject.org latest main
|
||||
49
config/torrc
Normal file
49
config/torrc
Normal file
@@ -0,0 +1,49 @@
|
||||
# Run Tor as a regular user (do not change this)
|
||||
#User debian-tor
|
||||
|
||||
TestingTorNetwork 1
|
||||
|
||||
## Comprehensive Bootstrap Testing Options ##
|
||||
# These typically launch a working minimal Tor network in 25s-30s,
|
||||
# and a working HS Tor network in 40-45s.
|
||||
# See authority.tmpl for a partial explanation
|
||||
#AssumeReachable 0
|
||||
#Default PathsNeededToBuildCircuits 0.6
|
||||
#Disable TestingDirAuthVoteExit
|
||||
#Disable TestingDirAuthVoteHSDir
|
||||
#Default V3AuthNIntervalsValid 3
|
||||
|
||||
## Rapid Bootstrap Testing Options ##
|
||||
# These typically launch a working minimal Tor network in 6s-10s
|
||||
# These parameters make tor networks bootstrap fast,
|
||||
# but can cause consensus instability and network unreliability
|
||||
# (Some are also bad for security.)
|
||||
AssumeReachable 1
|
||||
PathsNeededToBuildCircuits 0.25
|
||||
TestingDirAuthVoteExit *
|
||||
TestingDirAuthVoteHSDir *
|
||||
V3AuthNIntervalsValid 2
|
||||
|
||||
## Always On Testing Options ##
|
||||
# We enable TestingDirAuthVoteGuard to avoid Guard stability requirements
|
||||
TestingDirAuthVoteGuard *
|
||||
# We set TestingMinExitFlagThreshold to 0 to avoid Exit bandwidth requirements
|
||||
TestingMinExitFlagThreshold 0
|
||||
# VoteOnHidServDirectoriesV2 needs to be set for HSDirs to get the HSDir flag
|
||||
#Default VoteOnHidServDirectoriesV2 1
|
||||
|
||||
## Options that we always want to test ##
|
||||
Sandbox 1
|
||||
|
||||
# Private tor network configuration
|
||||
RunAsDaemon 0
|
||||
ConnLimit 60
|
||||
ShutdownWaitLength 0
|
||||
#PidFile /var/lib/tor/pid
|
||||
Log info stdout
|
||||
ProtocolWarnings 1
|
||||
SafeLogging 0
|
||||
DisableDebuggerAttachment 0
|
||||
|
||||
DirPortFrontPage /usr/share/doc/tor/tor-exit-notice.html
|
||||
|
||||
BIN
doc/arm.png
Normal file
BIN
doc/arm.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 83 KiB |
160
docker-compose.yml
Normal file
160
docker-compose.yml
Normal file
@@ -0,0 +1,160 @@
|
||||
version: '3'
|
||||
services:
|
||||
da1:
|
||||
build:
|
||||
context: .
|
||||
dockerfile: Dockerfile
|
||||
args:
|
||||
NICKNAME: ${DA1_NICKNAME}
|
||||
environment:
|
||||
ROLE: DA
|
||||
DA1_NICKNAME: DA1
|
||||
|
||||
|
||||
volumes:
|
||||
## Needed to keep track of other nodes
|
||||
- ./tor:/tor
|
||||
- ./keys:/keys
|
||||
|
||||
command: >
|
||||
sh -c "
|
||||
echo $DA1_NICKNAME &&
|
||||
mkdir -p /tor/$DA1_NICKNAME/keys &&
|
||||
cp -r /keys/* /tor/$DA1_NICKNAME/keys &&
|
||||
tor -f /etc/tor/torrc"
|
||||
|
||||
da2:
|
||||
build:
|
||||
context: .
|
||||
dockerfile: Dockerfile
|
||||
args:
|
||||
NICKNAME: ${DA2_NICKNAME}
|
||||
environment:
|
||||
ROLE: DA
|
||||
DA2_NICKNAME: DA2
|
||||
|
||||
|
||||
volumes:
|
||||
## Needed to keep track of other nodes
|
||||
- ./tor:/tor
|
||||
- ./keys:/keys
|
||||
|
||||
command: >
|
||||
sh -c "
|
||||
echo $DA2_NICKNAME &&
|
||||
mkdir -p /tor/$DA2_NICKNAME/keys &&
|
||||
cp -r /keys/* /tor/$DA2_NICKNAME/keys &&
|
||||
tor -f /etc/tor/torrc"
|
||||
|
||||
da3:
|
||||
build:
|
||||
context: .
|
||||
dockerfile: Dockerfile
|
||||
args:
|
||||
NICKNAME: ${DA3_NICKNAME}
|
||||
environment:
|
||||
ROLE: DA
|
||||
DA3_NICKNAME: DA3
|
||||
|
||||
|
||||
volumes:
|
||||
## Needed to keep track of other nodes
|
||||
- ./tor:/tor
|
||||
- ./keys:/keys
|
||||
|
||||
command: >
|
||||
sh -c "
|
||||
echo $DA3_NICKNAME &&
|
||||
mkdir -p /tor/$DA3_NICKNAME/keys &&
|
||||
cp -r /keys/* /tor/$DA3_NICKNAME/keys &&
|
||||
tor -f /etc/tor/torrc"
|
||||
|
||||
relay:
|
||||
image: tor-network:latest
|
||||
#expose:
|
||||
# - "7000"
|
||||
# - "9030"
|
||||
environment:
|
||||
ROLE: RELAY
|
||||
volumes:
|
||||
- ./tor:/tor
|
||||
depends_on:
|
||||
# Make sure the DA's are already up
|
||||
- da1
|
||||
- da2
|
||||
- da3
|
||||
- build_image
|
||||
exit:
|
||||
image: tor-network:latest
|
||||
#expose:
|
||||
# - "7000"
|
||||
# - "9030"
|
||||
environment:
|
||||
ROLE: EXIT
|
||||
volumes:
|
||||
- ./tor:/tor
|
||||
depends_on:
|
||||
# Make sure the DA's are already up
|
||||
- da1
|
||||
- da2
|
||||
- da3
|
||||
- build_image
|
||||
client:
|
||||
image: tor-network:latest
|
||||
ports:
|
||||
# Setups a listener on host machine
|
||||
- "9050:9050"
|
||||
- "9051:9051"
|
||||
volumes:
|
||||
- ./tor:/tor
|
||||
- ./keys:/keys
|
||||
environment:
|
||||
ROLE: CLIENT
|
||||
|
||||
command: >
|
||||
sh -c "
|
||||
mkdir -p /tor/$(hostname)/keys &&
|
||||
cp -r /keys /tor/$(hostname) &&
|
||||
tor -f /etc/tor/torrc"
|
||||
depends_on:
|
||||
- da1
|
||||
- da2
|
||||
- da3
|
||||
- build_image
|
||||
hs:
|
||||
image: tor-network:latest
|
||||
#expose:
|
||||
# - "80"
|
||||
environment:
|
||||
ROLE: HS
|
||||
# This will create a hidden service that points to
|
||||
# the service "web" which is runing nginx. You can
|
||||
# change this to whatever ip or hostname you want
|
||||
TOR_HS_PORT: "80"
|
||||
TOR_HS_ADDR: "web"
|
||||
volumes:
|
||||
- ./tor:/tor
|
||||
depends_on:
|
||||
- da1
|
||||
- da2
|
||||
- da3
|
||||
- build_image
|
||||
links:
|
||||
- web
|
||||
web:
|
||||
image: nginx
|
||||
#expose:
|
||||
# - "80"
|
||||
|
||||
|
||||
|
||||
build_image:
|
||||
build:
|
||||
context: .
|
||||
dockerfile: Dockerfile
|
||||
volumes:
|
||||
## Needed to keep track of other nodes
|
||||
- ./tor:/tor
|
||||
image: tor-network:latest
|
||||
command: ["/bin/true"]
|
||||
|
||||
45
keys/authority_certificate
Normal file
45
keys/authority_certificate
Normal file
@@ -0,0 +1,45 @@
|
||||
dir-key-certificate-version 3
|
||||
fingerprint 7EB85B97333C276E7D88000F074DFCD534CE69E2
|
||||
dir-key-published 2024-07-30 22:40:50
|
||||
dir-key-expires 2025-07-30 22:40:50
|
||||
dir-identity-key
|
||||
-----BEGIN RSA PUBLIC KEY-----
|
||||
MIIBigKCAYEAzr7AjPNjZv3I6GTGRV+Azn6FB4xDpm73aaIYqGTQIq+/Qi1Ot0P4
|
||||
t1Vmil0eXxRCqsoRDVNKzi+6FSAvvbnFocbMHd85y6iJawAJNO3Pt8F2dORZO+ya
|
||||
GMQv9/5ZiYAYYvGyruJwbJEf77jxSnlm95lOr25JdWTHq+53dZCLP7AK1SPsGdZy
|
||||
ZUlV0U1QwnvTpVE5PQPQMN+tRfeqAI2LENPLdGQjU4Msys39VWXt6FUdwVoX0VAl
|
||||
MZ62GYoFRATXG8z+OwHxjNe8GEyhPuVrLWxCGGE9rGvp3M57TjN0W+F0REYYq704
|
||||
EOvryzDUECuYODVssqZx8kcpIzIhNFe9R9ycd0hfowJd51kWSwWvQpY3IvZ6AGhQ
|
||||
JopS0JJTIeo0sLceldsbd+f7C8nBq7R+uQfX8J6BTWx88JLcmJ3gwi23bsZY98Dx
|
||||
vIo/Q+cVNJyVMtMHrqeqimgMA7I/qc16ru7ke0O2qNmUqeOTkIJItN3Aeu0yhAzB
|
||||
mwTWcgPfW+U1AgMBAAE=
|
||||
-----END RSA PUBLIC KEY-----
|
||||
dir-signing-key
|
||||
-----BEGIN RSA PUBLIC KEY-----
|
||||
MIIBCgKCAQEArQbVX2pXYtYANevfNnOJQ8D0/pGCxTxIIk6JA+YhVYazgLfLPktA
|
||||
naKBnXpZyntuApyKXqwhSN3PemnGzwE1Nps2Cs8wJlqQGUvokcF0lmtfj+gTuyz4
|
||||
HYpEzD74W9oJe7cEbB/Ee8oFW/NE/xMH1Rr9SnBWSHH2n9XunJWpxhiHZ4u8vh1F
|
||||
0Uc4ycbgRwD2fpAOIkkI7piIc76YVPpbB2RWgKWbWv6iWW7Umffre0DrSqOzrCEq
|
||||
QuKPNLygoPPvrDSa36AJUfUqltFlzXoxDtVUn7hCZYWrUahXBWobUF0/jNVkvTpo
|
||||
niZ7U3RWtgiMgiKAMX0qoH87pU0kUxMbzQIDAQAB
|
||||
-----END RSA PUBLIC KEY-----
|
||||
dir-key-crosscert
|
||||
-----BEGIN ID SIGNATURE-----
|
||||
pCFFAuM5oQNpIGzcdSGnoU2cImKIVcpw6asu2KiFTM+QRnLUS5ZgVEt7FpSQrMO3
|
||||
pe1sOj1RtqASAu8pyqLRrGcxukxHmYLA/og13X2ODhgdazA1tNFnuQqe0SZR9jct
|
||||
5QWu0Mp+p3SMnfxRP91DF8Sx0au7w9M7kfHBO3Wcur2F/lX8LMcMAB3P34Mw8hWV
|
||||
Dw2irLUKpZk9KtAZ2RShUC4rZkd70ZlF/DMHcthj1PiJBLdQZgsermUPBLwl05SG
|
||||
emSy4YWL9gcTnF9ZreoPlgxjdQcBl7+CaAXd5KHXUnu+bECNLAazsLprr+NtvK9N
|
||||
NJstnB5KHI4CgzGIWFP0WA==
|
||||
-----END ID SIGNATURE-----
|
||||
dir-key-certification
|
||||
-----BEGIN SIGNATURE-----
|
||||
HTHxvVcN+4X2OhjN57HbE0j+A01nRLuV6bHZqbT5Be+FPNd6E9ACp2hpp3vQRggv
|
||||
xLp0xGZndUNMgu2nsnf3Rgn5DYjT1BqkdJkF+K5ICr4e6XekYsBnbHjtWgCq1yTl
|
||||
7bZjPwHotFtMitAojXaG56kFLjtoY1/c0c3HqWp4xsMfk2jss5JHoK5IQVee/ttp
|
||||
Ba/5X054zUy8Ar8ZvNEpcCx3Vat2IY79n+S4vJKHoroM5EE72FVBK4q5cj6bSlkK
|
||||
Am1BmIZsmJrhoSej2cFM+V5ReAdNv5s+GcFF1hnQPaidtqnwOb414L73iS68nfJp
|
||||
4dwPhtIDQdZjNTT1+mntpHBG4xSV7UeokDcARsSEQX7Pv7tA6ijTKGCASAg+3Z0h
|
||||
pp9ZTxxoAh1MwRfcCQp6qFTIkUVhg6yitDVT0B3BFkKeEXTZormO0aQ5w15JJEtu
|
||||
CfGfjw95D3otZ15Jgvgt+ylPVcvHriu9mZsnnSsifx8sv82ofBiEqCYWukzewU6B
|
||||
-----END SIGNATURE-----
|
||||
41
keys/authority_identity_key
Normal file
41
keys/authority_identity_key
Normal file
@@ -0,0 +1,41 @@
|
||||
-----BEGIN ENCRYPTED PRIVATE KEY-----
|
||||
MIIHKjAcBgoqhkiG9w0BDAEDMA4ECGYCxeapu9jtAgIIAASCBwiGzFUv9++fl9UK
|
||||
VI0R+aKh34l7Q7LEklPwCNVBYochpLqbvX/7oNKEixCkJtvWaPFZC4AoUUZYVHww
|
||||
0am5w+pk6fUkZTz9yb9LItlz5yxhp0PotkKovoE08tJIepzQGLRPqhGhR6IuYeRm
|
||||
2UlZQwcn20IUQEeCpER/Z9DPETb1xHrledKKNZTlhQrT4F78HrEJvLFMqX0Q47IK
|
||||
crWO1GUn6pHiWgk0lRbyAnC6hVvup6NwTbDcdfcz9B55KSriqNcqCjnGsTiwqSv9
|
||||
nugydnAsAz8CswKJgsVojWounB0DPXWKnk3Q5JfijzDlvy9GCbvm9F8VbodrhQ0S
|
||||
NXXLs2SLRq+A6GYDGcpxsd5HBuMI8hde37fXo1DLImgvolEUiQccDgB98cf4n9IW
|
||||
e4PcG1a50IaXBCqrmhN18fReyf2HN3bne1OQcwzvMsQlFKXoa5Hs0297YcszDi+I
|
||||
3/88Ir5wRds5bAylukDSQzETvEDEN58C6d9ItRIAPMk8ti0ZY4ZxLKdATeNp9bBi
|
||||
SdhX/wDAyZeHxTSgC8FKNIY3/DVCnx0y4fvGEoFFjfoIxiR8PkajmJ4NurVvRKpw
|
||||
1Ft4s5L9iw4XdTmZJzN9ip+NUtXabNYeSLsRck7+AO/y6PdVCq2Md5ivd9OG9/y+
|
||||
YXjeSF53wXHzACs7IrM5c6/zaBhSAlSGmDNst6v/xQB6DBin9jA4OCSBvlPpkl7m
|
||||
57n91f8Rq0/rsxjFJ69Snu81SSNv3ltLF/gN6yzP+a9BEhd1yC9rSJb6xK5Ie/OJ
|
||||
ekxI51Nwo9y0SXVpM6cNjtCeyGZf1jIwLui574yRdl13YPZDf9ghFvtJH3vRuJpc
|
||||
7hGzpWBdSPiLrdwaA3t3/+iF00NVksiXwEtU0C4jB6pI8ZmbU4IOQz5AyNypB8rp
|
||||
xuDK9F5hf0fdDQJNZeigxWcznMESAOvANXT86iU4dKZ/KV62L3tEc1mRjrIRsWev
|
||||
lxlFojb+/RAT3sz++4CqjO8ot2iwWO+7xyMh7s/040Omt8wSTG5r2TeWIMRoApuL
|
||||
AU2yTB4ebD2dQoHGPUovMh2Y+E1ZMOQ5968/kKgfe+GLU8DpblTA2tw3bRj/I/yK
|
||||
fEjP0C0gg0XmtZ/SAEbddEnEuPOMLhv65wL1livZ7+EFklXrD4+nXntpwSuZK2l8
|
||||
Zae2LcB2uYDioxpeRXcm/WL7T3hpXzXkHTpJU8vdVZK3rlsSVbK6M3fQM3P2vyk/
|
||||
5gI3ub2ICzqtdF2FRWllXxV+qoJOwc8k0L3qN5ZDqP2QvC9/ce5Eemd1TpggQ3eb
|
||||
ITlqc7Ru5vB1h+FLXZObm72RsaQSJWHT/zg7e7o761c5fImVUesRDd0Mgetn3ZDi
|
||||
XHRAkRmEoPsUkN4znmjwB/0episoyhy2TG4Q+mNKGyESglTWjyamlPBOyjl3DDRJ
|
||||
BkG92fcj1q02+7yJpAVhQlYq5BGQdKkZYBKOuNNGglwaFqGqiTOfjrkA3eFZmCQB
|
||||
XuUte6kLk6AS2p6iJ20y6dYBXpU7E9DqaM/jSe1gz5a9rh9q7efbE90JLeu61sUi
|
||||
M1SgiSoczQ9hLuou9bdg1K0+PxAzxP0bAVqZ2YgPlI/ZhLy2bcWa/YPuSaybJrwx
|
||||
0sQ1bTbTy1P6s79DlWsHciw5G6m8ot1hyUZNfiryN3rEEkIHTNAkgKjXMtq34o+E
|
||||
qCYLELvmYVpaS0rjhByIHX+b1csB4tnsIGJasdj6MIk8ic2Ctp/grykbjUATO6vT
|
||||
J9NDt0OgERWV8wUvcBFkTDNqNoyG51K4EFVfzcI9R+5HaK4yxW3GjZA0VNRm2w2c
|
||||
kelxf4ySuO+M5Hwy4BwOfQwXWoREBeHCWZ7L/y7dZjAAM7lK7K28k0LAgP571Dpl
|
||||
D+pw0agyLTpd4w2ZSQOssKV6vZzIAsQ5r9vhz5o9GStCb/V3JtBtVZRHTqpjEPnR
|
||||
6iGS6jQx7ShLU2s1cVx0fn4LnJpCk1EoCbTH9AN4+P1Ubl/Y7O9Ux7MScQPbpTiX
|
||||
gvnkOR1Nc+WAL/BnGhO4MVAzyy6J6ogFsynRdJumCgzJdA9GgXWM3XSY1JGkVt8b
|
||||
Cyk5BktxTHiysZ/wljAnTK4eE/ynj6SyTDxiVsrhSMi07VXKeKb4HLMEZi35pCGz
|
||||
q4Lp33N4js1EtLDU89kKC5oX0z54tHDoLMLecaTGOJUCt2dh2/KEefFywrd4Rf5e
|
||||
H5GW7osLAYk7AqlhAYaQaAMadDs1pWJSiAXdfnePYBONYLERJbzeMA8q1P9c+R7r
|
||||
jgMcOoobBKvF0mBvY+SGhl8XrHjEgeeOr2sNtyk4NlJEqu9NQ0WKoECeLdA2afso
|
||||
Iue9LAPGmGgPf9MRvF8cyuyVW5V60iiHHvnOY4DWL5fAijgqPImchup88qGQ3voW
|
||||
/RLZprr8F4pi6m4QPng=
|
||||
-----END ENCRYPTED PRIVATE KEY-----
|
||||
27
keys/authority_signing_key
Normal file
27
keys/authority_signing_key
Normal file
@@ -0,0 +1,27 @@
|
||||
-----BEGIN RSA PRIVATE KEY-----
|
||||
MIIEpAIBAAKCAQEArQbVX2pXYtYANevfNnOJQ8D0/pGCxTxIIk6JA+YhVYazgLfL
|
||||
PktAnaKBnXpZyntuApyKXqwhSN3PemnGzwE1Nps2Cs8wJlqQGUvokcF0lmtfj+gT
|
||||
uyz4HYpEzD74W9oJe7cEbB/Ee8oFW/NE/xMH1Rr9SnBWSHH2n9XunJWpxhiHZ4u8
|
||||
vh1F0Uc4ycbgRwD2fpAOIkkI7piIc76YVPpbB2RWgKWbWv6iWW7Umffre0DrSqOz
|
||||
rCEqQuKPNLygoPPvrDSa36AJUfUqltFlzXoxDtVUn7hCZYWrUahXBWobUF0/jNVk
|
||||
vTponiZ7U3RWtgiMgiKAMX0qoH87pU0kUxMbzQIDAQABAoIBAASZWAkwckZyHlx/
|
||||
F7lCp4sLzldCyA0AfphXkrActMQGbN5d8s5XTRQPL308kin1OAMHTbLH3UxB7oIs
|
||||
f6zL5ANtVBJyqXTWbmX/6e3sxpSulggTl1JOXNLZowvcv1iTemCYq1Zgk2vl/m/W
|
||||
GnKzkkrcYGE76Z55PnIkKFWdPPPDFcwFYmk/oCBR+Rn5YtteUHFJfHMZlE9clG6h
|
||||
m3fw3QKQn43LcMJJveiI2ISkBAq0Y4aqDGNR95Z13z8MqqqZwbJlmKMk4O5dM82p
|
||||
2UdvwEAvAm+AhQYjozT2LWI/lO6TkzcUHTyjFmgIdCb2vb0XGqfI0hZ5hXoOlmM3
|
||||
TgbS0B8CgYEAvFXWtbqtZ4aAOvrN9plppNISB8ywxD7E4ErWVdUnFZPR9XqWTbyk
|
||||
IA6p7Q+GWdKy2InpcmvCWgbkopX3gHYj7QbBfpTSVu7CPnqY2LcorOC6QuHZwPkR
|
||||
Qfo1oszbOjdN4rmQ58ClGx52p5ERCgbd/Zgpv4qyFtBJbiTGS9dbiZMCgYEA6zD7
|
||||
tmD/zU5WKBuTC/Fa7q4xXOwJ9MZ2L7URtwTsamOuLWRlfPd3KFgxL+vXMweYgctd
|
||||
WPwnouMqlWIpSA+1oIwMj1PfaHGRcoGOHHI2LI3RyqMs8GO4Xs5RFf6bYnQ96A/a
|
||||
oumar+lppV10WBJhr6SAqDnVBI0c5O5iryeooR8CgYA9V7AhbPZB+/sUOtCO+5T/
|
||||
TDT3OWJx6QfzDi0Vs+GRE56VWCJQm5rRnjUWs7HM2+XIxdK1pAefjxM1Kad9vf0h
|
||||
nMu1UP/ZtNarxv61x6KF/IRueGWWhwlp9fc2WYcmRREnQc3Czmp4lMmM9qEYJPh1
|
||||
OvSOILy01Y61Q2EbHr//5QKBgQCOTGC/hAjBSzhNpAFgJHOEHdi4BAgyFTHEw6Uo
|
||||
Os5fwFfOFwRgi8mIm3OHLwZRVbMsNMMR596DazaEk5OuifK2ZIXk4jY1lyENSt2U
|
||||
0HV+l3/rPrcd6vfORL5CtH2HIBWkppL+JqD09iB5cQXHk7eO8dT186eyzT5CNQl4
|
||||
OGKKuQKBgQCgrTNN1GF9rJ3x8Kf7Se6fMc2kBkU0B5biwapDER+iriW3BkHbUp47
|
||||
32QP5HBKnbvbBhTfB/99VrwLbnU6cFW/qICXdQo6b2J30PehNWzOFcl5vKRIb1Pc
|
||||
UrpwQpZWX/+XnpflVtKrEMegkK/p3KBqOvoXRC9NNJET0+OXuuvtVg==
|
||||
-----END RSA PRIVATE KEY-----
|
||||
BIN
keys/ed25519_master_id_public_key
Normal file
BIN
keys/ed25519_master_id_public_key
Normal file
Binary file not shown.
BIN
keys/ed25519_master_id_secret_key
Normal file
BIN
keys/ed25519_master_id_secret_key
Normal file
Binary file not shown.
BIN
keys/ed25519_signing_cert
Normal file
BIN
keys/ed25519_signing_cert
Normal file
Binary file not shown.
BIN
keys/ed25519_signing_secret_key
Normal file
BIN
keys/ed25519_signing_secret_key
Normal file
Binary file not shown.
BIN
keys/secret_id_key
Normal file
BIN
keys/secret_id_key
Normal file
Binary file not shown.
BIN
keys/secret_onion_key
Normal file
BIN
keys/secret_onion_key
Normal file
Binary file not shown.
BIN
keys/secret_onion_key_ntor
Normal file
BIN
keys/secret_onion_key_ntor
Normal file
Binary file not shown.
12
scripts/da_fingerprint
Normal file
12
scripts/da_fingerprint
Normal file
@@ -0,0 +1,12 @@
|
||||
#!/bin/sh
|
||||
# version 2
|
||||
TOR_NICK=$(grep "^Nick" /etc/tor/torrc | awk -F ' ' '{print $2}')
|
||||
AUTH=$(grep "fingerprint" $TOR_DIR/$TOR_NICK/keys/* | awk -F " " '{print $2}')
|
||||
NICK=$(cat $TOR_DIR/$TOR_NICK/fingerprint| awk -F " " '{print $1}')
|
||||
RELAY=$(cat $TOR_DIR/$TOR_NICK/fingerprint|awk -F " " '{print $2}')
|
||||
SERVICE=$(grep "dir-address" $TOR_DIR/$TOR_NICK/keys/* | awk -F " " '{print $2}')
|
||||
IPADDR=$(ip addr | grep 'state UP' -A2 | tail -n1 | awk '{print $2}' | cut -f1 -d'/')
|
||||
|
||||
TORRC="DirAuthority $TOR_NICK orport=${TOR_ORPORT} no-v2 v3ident=$AUTH $SERVICE $RELAY"
|
||||
|
||||
echo $TORRC
|
||||
107
scripts/docker-entrypoint
Normal file
107
scripts/docker-entrypoint
Normal file
@@ -0,0 +1,107 @@
|
||||
#!/bin/bash
|
||||
set -o errexit
|
||||
|
||||
# Fudge the sleep to try and keep the consensus
|
||||
#FUDGE=$(( ( RANDOM % 100) + 20 ))
|
||||
FUDGE=3
|
||||
|
||||
echo -e "\n========================================================"
|
||||
|
||||
if [ ! -e /tor-config-done ]; then
|
||||
touch /tor-config-done # only run this once
|
||||
|
||||
# Generate a random name
|
||||
RPW=$(pwgen -0A 10)
|
||||
export TOR_NICKNAME=${ROLE}${RPW}
|
||||
echo "Setting random Nickname: ${TOR_NICKNAME}"
|
||||
echo -e "\nNickname ${TOR_NICKNAME}" >> /etc/tor/torrc
|
||||
|
||||
# Host specific modifications to the torrc file
|
||||
echo -e "DataDirectory ${TOR_DIR}/${TOR_NICKNAME}" >> /etc/tor/torrc
|
||||
# Updated to handle docker stack/swarm network overlays
|
||||
TOR_IP=$(ip addr show eth1 | grep "inet" | grep -v '\/32'| awk '{print $2}' | cut -f1 -d'/')
|
||||
NICS=$(ip addr | grep 'state UP' | awk '{print $2}' | cut -f1 -d':')
|
||||
|
||||
echo "Address ${TOR_IP}" >> /etc/tor/torrc
|
||||
echo -e "ControlPort 0.0.0.0:9051" >> /etc/tor/torrc
|
||||
if [ -z "${TOR_CONTROL_PWD}" ]; then
|
||||
TOR_CONTROL_PWD="16:6971539E06A0F94C6011414768D85A25949AE1E201BDFE10B27F3B3EBA"
|
||||
fi
|
||||
echo -e "HashedControlPassword ${TOR_CONTROL_PWD}" >> /etc/tor/torrc
|
||||
|
||||
# Changes to the torrc file based on the desired role
|
||||
case ${ROLE} in
|
||||
DA)
|
||||
echo "Setting role to DA"
|
||||
cat /etc/tor/torrc.da >> /etc/tor/torrc
|
||||
echo -e "OrPort ${TOR_ORPORT}" >> /etc/tor/torrc
|
||||
echo -e "Dirport ${TOR_DIRPORT}" >> /etc/tor/torrc
|
||||
echo -e "ExitPolicy accept *:*" >> /etc/tor/torrc
|
||||
KEYPATH=${TOR_DIR}/${TOR_NICKNAME}/keys
|
||||
mkdir -p ${KEYPATH}
|
||||
echo "password" | tor-gencert --create-identity-key -m 12 -a ${TOR_IP}:${TOR_DIRPORT} \
|
||||
-i ${KEYPATH}/authority_identity_key \
|
||||
-s ${KEYPATH}/authority_signing_key \
|
||||
-c ${KEYPATH}/authority_certificate \
|
||||
--passphrase-fd 0
|
||||
tor --list-fingerprint --orport 1 \
|
||||
--dirserver "x 127.0.0.1:1 ffffffffffffffffffffffffffffffffffffffff" \
|
||||
--datadirectory ${TOR_DIR}/${TOR_NICKNAME}
|
||||
echo "Saving DA fingerprint to shared path"
|
||||
da_fingerprint >> ${TOR_DIR}/torrc.da
|
||||
echo "Waiting for other DA's to come up..."
|
||||
;;
|
||||
RELAY)
|
||||
echo "Setting role to RELAY"
|
||||
echo -e "OrPort ${TOR_ORPORT}" >> /etc/tor/torrc
|
||||
echo -e "Dirport ${TOR_DIRPORT}" >> /etc/tor/torrc
|
||||
echo -e "ExitPolicy accept private:*" >> /etc/tor/torrc
|
||||
|
||||
echo "Waiting for other DA's to come up..."
|
||||
;;
|
||||
EXIT)
|
||||
echo "Setting role to EXIT"
|
||||
echo -e "OrPort ${TOR_ORPORT}" >> /etc/tor/torrc
|
||||
echo -e "Dirport ${TOR_DIRPORT}" >> /etc/tor/torrc
|
||||
echo -e "ExitPolicy accept *:*" >> /etc/tor/torrc
|
||||
echo "Waiting for other DA's to come up..."
|
||||
;;
|
||||
CLIENT)
|
||||
echo "Setting role to CLIENT"
|
||||
echo -e "SOCKSPort 0.0.0.0:9050" >> /etc/tor/torrc
|
||||
;;
|
||||
HS)
|
||||
# NOTE By default the HS role will point to a service running on port 80
|
||||
# but there is no service running on port 80. You can either attach to
|
||||
# the container and start one, or better yet, point to another docker
|
||||
# container on the network by setting the TOR_HS_ADDR to its IP
|
||||
echo "Setting role to HIDDENSERVICE"
|
||||
echo -e "HiddenServiceDir ${TOR_DIR}/${TOR_NICKNAME}/hs" >> /etc/tor/torrc
|
||||
if [ -z "${TOR_HS_PORT}" ]; then
|
||||
TOR_HS_PORT=80
|
||||
fi
|
||||
if [ -z "${TOR_HS_ADDR}" ]; then
|
||||
TOR_HS_ADDR=127.0.0.1
|
||||
fi
|
||||
echo -e "HiddenServicePort ${TOR_HS_PORT} ${TOR_HS_ADDR}:${TOR_HS_PORT}" >> /etc/tor/torrc
|
||||
;;
|
||||
*)
|
||||
echo "Role variable missing"
|
||||
exit 1
|
||||
;;
|
||||
esac
|
||||
|
||||
# Buffer to let the directory authority list be built
|
||||
sleep $FUDGE
|
||||
cat ${TOR_DIR}/torrc.da >> /etc/tor/torrc
|
||||
|
||||
fi
|
||||
|
||||
echo -e "\n========================================================"
|
||||
# display Tor version & torrc in log
|
||||
tor --version
|
||||
cat /etc/tor/torrc
|
||||
echo -e "========================================================\n"
|
||||
|
||||
# else default to run whatever the user wanted like "bash"
|
||||
exec "$@"
|
||||
47
torrc.da.template
Normal file
47
torrc.da.template
Normal file
@@ -0,0 +1,47 @@
|
||||
AuthoritativeDirectory 1
|
||||
V3AuthoritativeDirectory 1
|
||||
|
||||
# Speed up the consensus cycle as fast as it will go
|
||||
# Voting Interval can be:
|
||||
# 10, 12, 15, 18, 20, 24, 25, 30, 36, 40, 45, 50, 60, ...
|
||||
# Testing Initial Voting Interval can be:
|
||||
# 5, 6, 8, 9, or any of the possible values for Voting Interval,
|
||||
# as they both need to evenly divide 30 minutes.
|
||||
# If clock desynchronisation is an issue, use an interval of at least:
|
||||
# 18 * drift in seconds, to allow for a clock slop factor
|
||||
TestingV3AuthInitialVotingInterval 300
|
||||
#V3AuthVotingInterval 15
|
||||
# VoteDelay + DistDelay must be less than VotingInterval
|
||||
TestingV3AuthInitialVoteDelay 5
|
||||
V3AuthVoteDelay 5
|
||||
TestingV3AuthInitialDistDelay 5
|
||||
V3AuthDistDelay 5
|
||||
# This is autoconfigured by chutney, so you probably don't want to use it
|
||||
#TestingV3AuthVotingStartOffset 0
|
||||
|
||||
# Work around situations where the Exit, Guard and HSDir flags aren't being set
|
||||
# These flags are all set eventually, but it takes Guard up to ~30 minutes
|
||||
# We could be more precise here, but it's easiest just to vote everything
|
||||
# Clients are sensible enough to filter out Exits without any exit ports,
|
||||
# and Guards and HSDirs without ORPorts
|
||||
# If your tor doesn't recognise TestingDirAuthVoteExit/HSDir,
|
||||
# either update your chutney to a 2015 version,
|
||||
# or update your tor to a later version, most likely 0.2.6.2-final
|
||||
|
||||
# These are all set in common.i in the Comprehensive/Rapid sections
|
||||
# Work around Exit requirements
|
||||
#TestingDirAuthVoteExit *
|
||||
# Work around bandwidth thresholds for exits
|
||||
#TestingMinExitFlagThreshold 0
|
||||
# Work around Guard uptime requirements
|
||||
#TestingDirAuthVoteGuard *
|
||||
# Work around HSDir uptime and ORPort connectivity requirements
|
||||
#TestingDirAuthVoteHSDir *
|
||||
|
||||
Address 127.0.0.1
|
||||
DirAuthority Alex 127.0.0.1:9030 7EB85B97333C276E7D88000F074DFCD534CE69E2
|
||||
|
||||
Nickname ${NICKNAME}
|
||||
DataDirectory /tor/${NICKNAME}
|
||||
|
||||
# Nickname ${TOR_NICKNAME}
|
||||
12
util/README.md
Normal file
12
util/README.md
Normal file
@@ -0,0 +1,12 @@
|
||||
## Utils
|
||||
|
||||
This folder contains various scripts to let you perform
|
||||
functions on your tor instance. Many of these are from the
|
||||
[Stem Website](https://stem.torproject.org) which has
|
||||
additional documentation on functions you can perform.
|
||||
|
||||
Other examples:
|
||||
|
||||
Use tor-prompt to interact with a docker process:
|
||||
|
||||
```tor-prompt -i 172.16.0.3:9051``
|
||||
42
util/control_port.py
Normal file
42
util/control_port.py
Normal file
@@ -0,0 +1,42 @@
|
||||
# Connects to the control port to test that the private network is working
|
||||
import getpass
|
||||
import sys
|
||||
|
||||
import stem
|
||||
import stem.connection
|
||||
|
||||
from stem.control import Controller
|
||||
|
||||
if __name__ == '__main__':
|
||||
try:
|
||||
controller = Controller.from_port()
|
||||
except stem.SocketError as exc:
|
||||
print("Unable to connect to tor on port 9051: %s" % exc)
|
||||
sys.exit(1)
|
||||
|
||||
try:
|
||||
controller.authenticate()
|
||||
except stem.connection.MissingPassword:
|
||||
pw = getpass.getpass("Controller password: ")
|
||||
|
||||
try:
|
||||
controller.authenticate(password = pw)
|
||||
except stem.connection.PasswordAuthFailed:
|
||||
print("Unable to authenticate, password is incorrect")
|
||||
sys.exit(1)
|
||||
except stem.connection.AuthenticationFailure as exc:
|
||||
print("Unable to authenticate: %s" % exc)
|
||||
sys.exit(1)
|
||||
|
||||
print("List of DAs found:")
|
||||
for desc in controller.get_network_statuses():
|
||||
print("found relay %s (%s)" % (desc.nickname, desc.address))
|
||||
|
||||
print("List of Relays Found:")
|
||||
for desc in controller.get_microdescriptors():
|
||||
print("found relay %s (%s)" % (desc.identifier, desc.or_addresses))
|
||||
|
||||
|
||||
|
||||
print("Tor is running version %s" % controller.get_version())
|
||||
controller.close()
|
||||
8
util/get_consensus.py
Normal file
8
util/get_consensus.py
Normal file
@@ -0,0 +1,8 @@
|
||||
from stem.control import Controller
|
||||
|
||||
with Controller.from_port(port = 9051) as controller:
|
||||
controller.authenticate("password")
|
||||
|
||||
print("List of relays found on the network:")
|
||||
for desc in controller.get_network_statuses():
|
||||
print("%s (%s) at %s" % (desc.nickname, desc.fingerprint, desc.address))
|
||||
9
util/read_consensus.py
Normal file
9
util/read_consensus.py
Normal file
@@ -0,0 +1,9 @@
|
||||
from stem.descriptor import parse_file
|
||||
import sys
|
||||
|
||||
try:
|
||||
path = sys.argv[1]
|
||||
for desc in parse_file(path):
|
||||
print('found relay %s (%s)' % (desc.nickname, desc.fingerprint))
|
||||
except IOError:
|
||||
print("File not found. make sure you supply it with a cached consensus file location: %s" % path)
|
||||
Reference in New Issue
Block a user